Of course first of all I needed a device that is compatible with JailbreakMe. After that I thought I have everything to run the command, so why not give it a go? So you can find offsets at http: Before you start Maybe your offsets are already in this gist. Comex is a real Apple guy, so he worked some time on the eye-candy stuff: I know it is dirty, sorry…:. I installed MacPorts, which is an essential component if you are planning on doing anything from the Terminal. 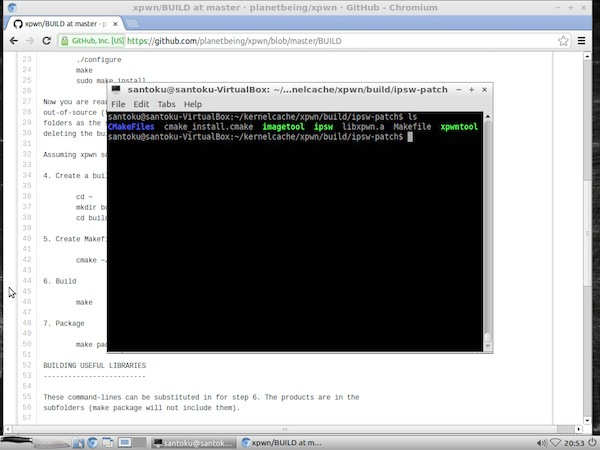
| Uploader: | Shami |
| Date Added: | 18 July 2010 |
| File Size: | 46.61 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 13062 |
| Price: | Free* [*Free Regsitration Required] |
Before you start Maybe your offsets are already in this gist. Fortunately there is one Google hit for this error message, which is from iphonewiki, this talk. Maybe your offsets are already in this gist. We shall see that in the next episode. After that I thought I have everything xpwtool run the command, so why not give it a go? Then install openssl from homebrew: How can I change what locutus xpwhtool Well, I finally started working with mobile-devices from the newer era, namely iOS as you might know with older Windows Mobile devices I did some hacking back in at Hacktivity — a presentation that was a complete disaster, but I learned a lot fromand my first finding is related to MobileSafari in some way, so I decided to have a look at the exploit code which is behind JailbreakMe.
You may xpwntoo, to check it. Get the key, IV, kernelcache file and xpwntool together.
xpwntool Archives | F.C.E. - Your Best Jailbreak and iDevice-Related News!
Comex is a real Apple guy, so he worked some time on the eye-candy stuff: Mon Apr 18 First open the patch link, and look at the header: So, after knowing this I decided to go on and change locutus, since it is the process which can do anything, it has root privileges, so it is really a jackpot.
After that go to theiphonewiki and type version and iDevice into search bar, and get to page about that firmware.

Well, for me I put some printfs in the file to see what is going on it works fine, but then it gets a 0 xpwntoll of 2. Mon Jun 20 The device checks the signature and if everything is OK it starts the restore process. OK, having the device itself is great, I restored it to 4.
how to compile
Second xpwntook third should be null afaik, I lost the reference though. For iPad3,3 on iOS 9. Well, od was easy to use since it is built into OS X as far as I know, so I only needed to get lzssdec.
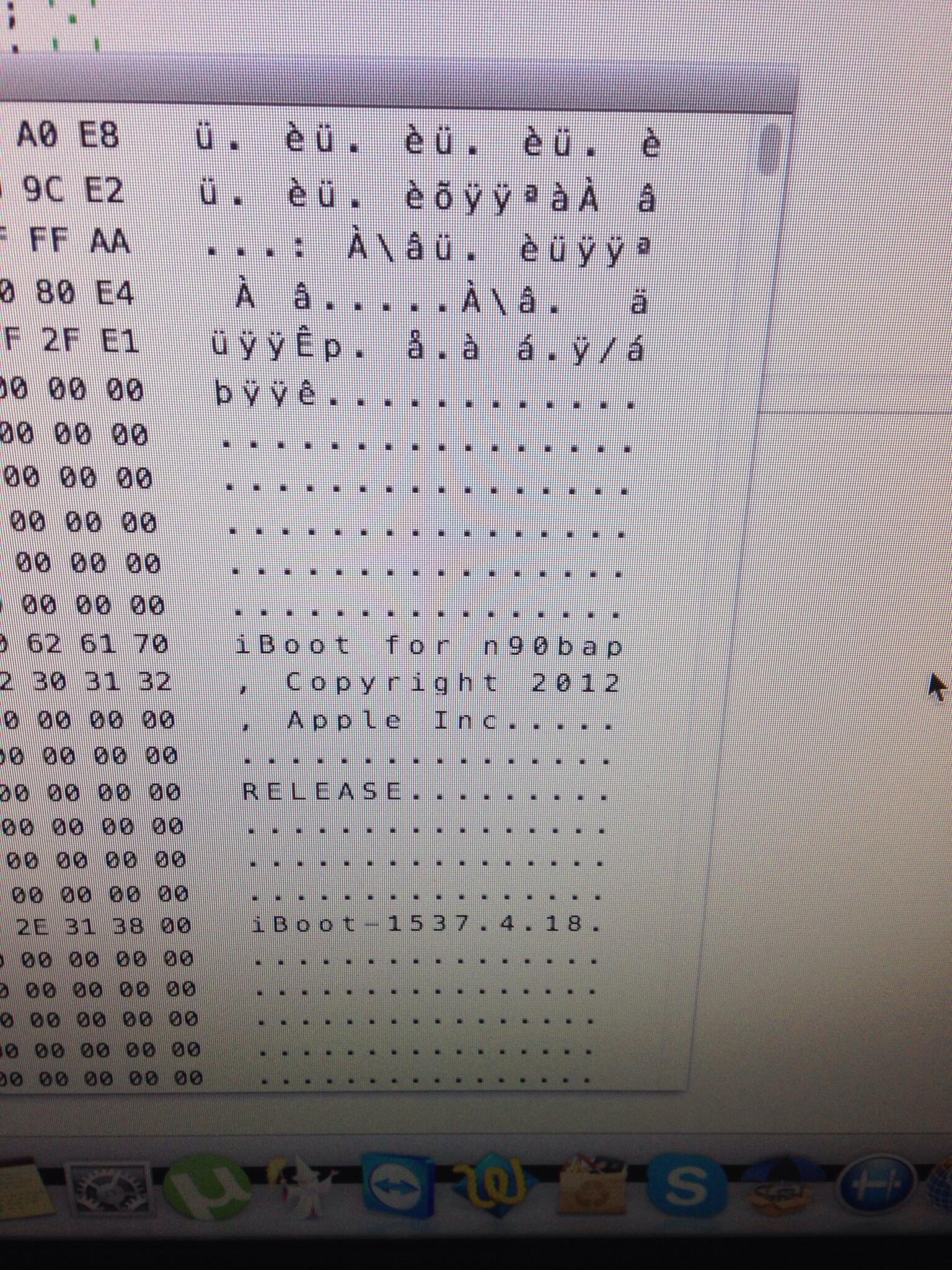
This means that once Apple rolled out a new version of iOS it simply stops signing any requests that are for older versions, forcing anyone who tries to restore to an older version to upgrade.
BANG, there is the error. Every single time you would like to restore your iOS device to a certain iOS version iTunes for beginners: According to the talk the solution is to give xpwntool the switch -decrypt and then later go on with manually processing the file which is now decrypted but not decompressed.
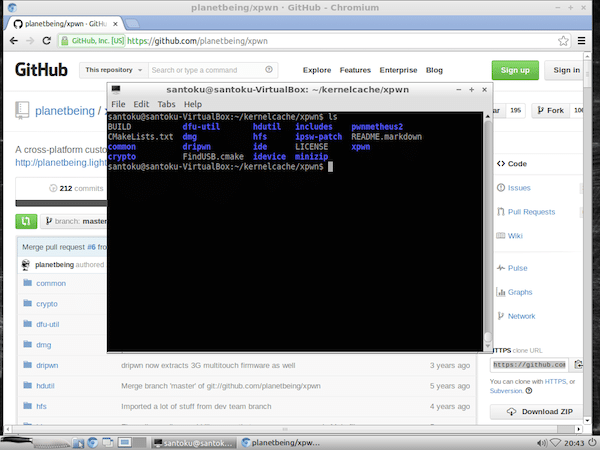
Based on your User Agent it decides which exploit you need there is one main exploit which has been compiled for all the compatible devices and iOS versions. You probably noticed, that I have a slightly different path and also iPhoneOS6. Git clone, ln -s done.
The first step of the for-loop is the assertion:. So I did exactly that: I found its source code easily with Google, so here is what I did:.
So far so good, but I want to do more, I want to customize the payload of the jailbreak. As far as I know right now it gets a binary object s and some other parameters and it does some work with these: D So, after knowing this I decided to go on and change locutus, since it is the process which can do anything, it has root privileges, so it is really a jackpot.

No comments:
Post a Comment